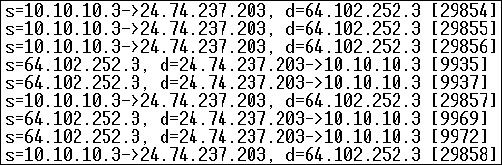
• change DDR from legacy to dialer profiles
• remove the dialer list statement from the configuration
* change the dialer list to exclude ICMP as interesting
• disable inverse ARP
2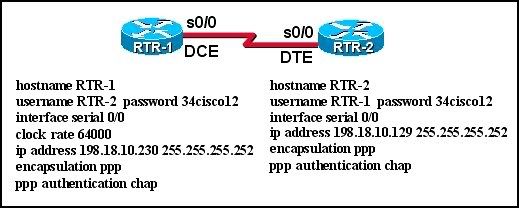
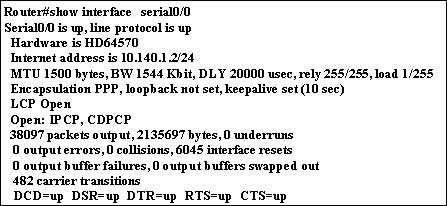
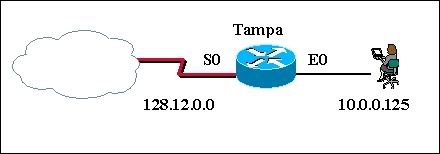
Refer to the exhibit. The link between the RTR-1 and RTR-2 routers is configured as shown in the exhibit. Although the show interfaces command shows the interface status as Serial0 is up, line protocol is up, IP traffic is not crossing this link. What is the problem?
• The usernames are misconfigured.
• The clock rate is configured on the wrong end of the link.
* The IP addresses are not in the same subnet.
• Interface serial 0/0 on RTR-1 must connect to interface serial 0/1 on RTR-2.
• The passwords must be different for the CHAP authentication.
• The clock rate must be 56000.
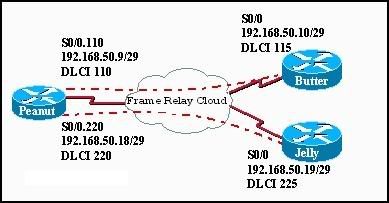
3 A technician enters the interface serial 0/0.1 multipoint command when configuring a router. What effect will the multipoint keyword have in this configuration? (Choose two.)
* Split-horizon issues will need to be resolved for this network if RIP is the routing protocol.
• A subinterface will be defined for each PVC.
* All the participating interfaces of remote routers will be configured in the same subnet.
• A single DLCI will be used to define all the PVCs to the remote routers.
• An IP address will need to be configured on the main interface.
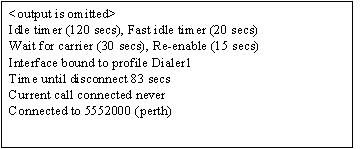
4 A branch office reports excessive connect time charges for an ISDN circuit used to connect to the regional office. Upon investigation of this issue, it is discovered that when an ISDN connection is initiated to the regional office it remains connected for an excessive amount of time. Which of the following configuration changes could be made to DDR on the router to reduce these connect time charges?
• use PPP multilink
* lower idle timer setting
• use CHAP authentication
• change DDR from legacy to dialer profiles
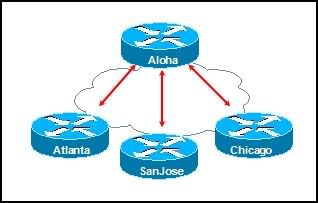
5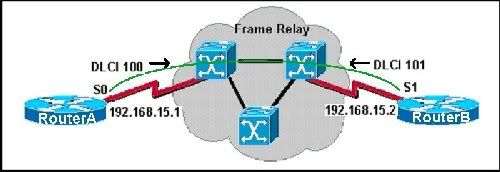
Which router command would be used to associate a Layer 2 address with the corresponding Layer 3 address in the internetwork in the diagram?
• RouterA(config-if)#frame-relay pvc 100 192.168.15.2
• RouterA(config-if)#dialer-map ip 192.168.15.1 100 broadcast
* RouterA(config-if)#frame-relay map ip 192.168.15.2 100 broadcast
• RouterA (config-if)#dialer-map 192.168.15.1 101 serial 0 broadcast
• RouterA (config-if)#frame-relay dlci 101 192.168.15.1 broadcast
• RouterA (config-if)#dialer-map 192.168.15.1 inverse-arp broadcast
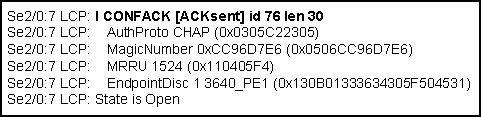
6 What does the output of the show frame-relay map command shown below represent? (Choose two.)
Serial 0 (up): ip 172.30.151.4 dlci 122, dynamic, broadcast, status defined, active
* 172.30.151.4 represents the IP address of the remote router.
• 172.30.151.4 represents the IP address of the local serial interface.
• DLCI 122 represents the interface of the remote router.
* broadcast indicates that a dynamic routing protocol such as RIP v1 can send packets across this PVC.
• dynamic indicates that a dynamic routing protocol is enabled for this connection.
• active indicates that the ARP process is working.
7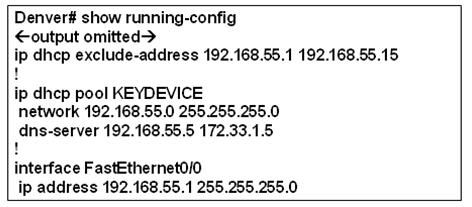
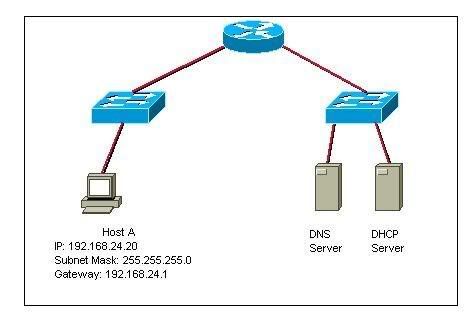
Refer to the exhibit. The network administrator of the Denver router has determined that the DHCP clients on the network are not working properly. The clients are receiving IP configuration information from a DHCP server configured on the router but cannot access the Internet. From the output in the exhibit, what is the most likely problem?
• The DHCP server service is not enabled.
• The DHCP pool is not bound to the interface.
• The inside interface for DCHP is not defined.
* The pool does not have a default router defined for the clients.
• All the host addresses have been excluded from the DHCP pool.
8 What are two ways to resolve split-horizon issues in a Frame Relay network? (Choose two.)
* create a full-mesh topology
• disable Inverse ARP
* use point-to-point subinterfaces
• use multipoint subinterfaces
• remove the broadcast keyword from the frame-relay map command
9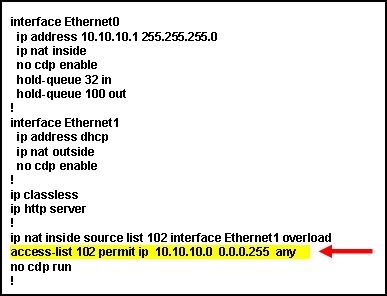
What is the purpose of the command marked with an arrow shown in the partial configuration output of a Cisco 806 broadband router?
• defines which addresses are allowed out of the router
• defines which addresses are allowed into the router
* defines which addresses can be translated
• defines which addresses are assigned to a NAT pool
10 Which scenarios present possible reasons for using the frame-relay map command when configuring a Frame Relay connection? (Choose two.)
* when dynamic mapping of DLCIs to IP addresses is not supported by the remote router
• when the local router is using IOS Release 11.1 or earlier
• when the remote router is a non-Cisco router
• when globally significant rather than locally significant DLCIs are being used
* when broadcast traffic and multicast traffic over the PVC must be controlled
11 While testing a new network design in the lab, a network administrator is configuring a serial link that connects two routers back-to-back. In order to finish the configuration, the administrator needs to identify which router is connected to the DCE end of the cable. What command can be issued to provide this information?
• router# show status serial 0/0
* router# show controllers serial 0/0
• router# show protocols serial 0/0
• router# show version
• router# show interfaces serial 0/0
12 Which statements are correct about the point in the network where the responsibility of the service provider ends? (Choose three.)
* The International point is on the customer side of the network terminating unit(NTU).
* The United States point is at the interface of the customer-provided equipment and the local loop.
• The responsibility for this point is controlled by IANA.
* The point is called the demarcation point.
• The point is typically located at the service provider's central office.
• The point is located between the customer's local area networks.
13
A system administrator is unable to ping the Serial0/0 interface of RouterB from RouterA. During the troubleshooting process, the following facts are established:
- IP addressing and subnet masks are correct.
- RouterA is a Cisco router and RouterB is a router from another vendor.
- RouterA is configured with the default encapsulation.
- The serial interfaces on both routers are up.
- The protocol is down on the serial interfaces of both routers.
What should the administrator do to solve the problem?
• Add a clock rate on RouterA.
• Enable the serial interface on RouterB.
* Change the encapsulation on both routers to PPP.
• Connect the serial cable to the correct interface on RouterB.
• Use the correct serial cable to attach the CSU/DSU to RouterB.
14 When a Frame Relay switch detects an excessive buildup of frames in its queue, which of the following may occur? (Choose two.)
* Frames with the DE bit set are dropped from the switch queue.
• Frames with the FECN and BECN bits set are dropped from the switch queue.
• Frames in excess of the CIR are not accepted by the switch.
• The switch sets the FECN bit on all frames it places on the congested link and sets the BECN bit on all frames it receives on the congested link.
* The switch sets the FECN bit on all frames it receives on the congested link and sets the BECN bit on all frames it places on the congested link.
15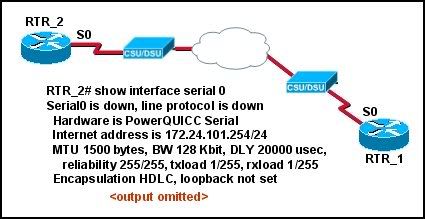
Refer to the exhibit. A network administrator is checking the status of router RTR_2. What is the most likely reason for the current status of the serial link to RTR_1?
* A cable has become disconnected.
• The circuit is experiencing excessive RFI.
• Authentication is not properly configured on the routers.
• The routers are configured for different WAN encapsulations.
• The clock rate is not properly configured on one of the routers.
16 What are two of the steps required to configure a router to connect over ISDN BRI? (Choose two.)
• Configure the interface with a DLCI.
* Configure the SPIDs, if required by the ISDN switch.
• Specify the the LMI type to be compatible with the CO switch.
• Set the interface encapsulation to the Cisco or IETF frame type.
• Configure a subinterface for each B channel.
* Set the switch type to work with the ISDN switch at the CO.
17 What value in the address field of a Frame Relay header identifies the destination of the frame?
• CIR
• DE
* DLCI
• ISDN
• FRAD
• PVC
18 Which of the following describes the roles of devices in a WAN? (Choose three.)
* A CSU/DSU terminates a digital local loop.
• A modem terminates a digital local loop.
• A CSU/DSU terminates an analog local loop.
* A modem terminates an analog local loop.
* A router is commonly considered a DTE device.
• A router is commonly considered a DCE device.
19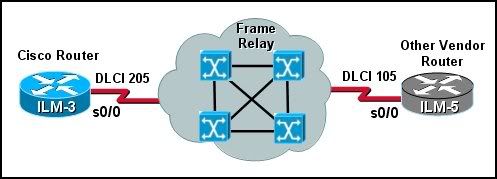
Refer to the exhibit. Two routers are connected through a Frame Relay point-to-point PVC. The ILM-5 router is from a vendor other than Cisco. Which interface command is required to configure the link between the Cisco ILM-3 router and router ILM-5?
• ILM-3(config-if)# encapsulation frame-relay cisco
• ILM-3(config-if)# frame-relay pvc multipoint
* ILM-3(config-if)# encapsulation frame-relay ietf
• ILM-3(config-if)# frame-relay lmi-type ansi
• ILM-3(config-if)# frame-relay pvc point-to-point
20 The output of the show interfaces serial 0/0 command for a frame-relay connection indicates that the serial line is up but the line protocol is down. What are possible causes for this? (Choose two.)
* There is an LMI-type mismatch between the Frame Relay switch and the router.
* There is no clock present on the serial interface.
• The interface is shut down.
• RARP is not functioning on the router.
• The cable is disconnected.
21 After configuring a dialup ISDN circuit, a network associate begins testing the dialup connection. When attempting to ping a host on the remote network, the local router does not attempt to dial the remote access server. Which of the following are possible errors in this configuration? (Choose three.)
• PPP authentication is not properly configured.
* No dialer map is configured.
• The ISDN circuit connected to the remote access server is busy.
* No interesting traffic is defined.
* No route is determined to the remote network.
• A wrong number is configured in the dial string.
22 When configuring a Frame Relay network with subinterfaces, which commands are configured on the subinterface? (Choose three.)
* frame-relay interface-dlci
• encapsulation frame-relay ietf
* ip address
* frame-relay map
• switch type
23 Below is a list of DDR steps. Which of the following identifies the proper order of DDR?
1 - dial number is looked up
2 - interesting traffic triggers DDR
3 - route to destination is determined
4 - call is made
• 1,2,3,4
• 1,3,2,4
• 2,3,1,4
• 2,1,3,4
* 3,2,1,4
• 3,1,2,4
24 A network administrator issued the command show frame-relay pvc. The response from the router shows the status of a PVC as deleted. What is the reason for this output?
• The DLCI is using the wrong LMI type.
• The DLCI is usable but has little activity.
• The DLCI is programmed in the switch but the circuit is not usable.
* The DLCI was formerly programmed in the switch but is no longer there.
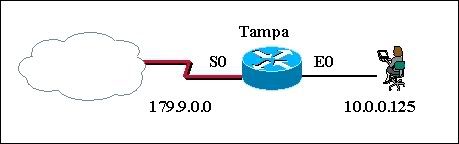
25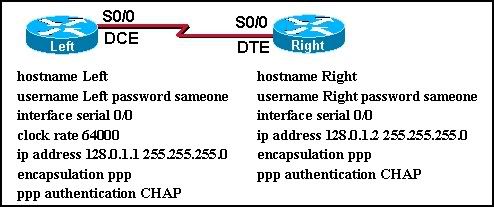
The serial PPP link between the Left and Right routers is configured as shown in the diagram. Which configuration issue explains why the link is unable to establish a PPP session
• The IP addresses must be on different subnets.
* The usernames are misconfigured.
• The passwords must be different for the CHAP authentication.
• The clock rate must be 56000.
• The clock rate is configured on the wrong end of the link.
• Interface serial 0/0 on Left must connect to interface serial 0/1 on Right.
26 Which protocol should be chosen to support WAN connectivity in a multi-vendor system and provide strong security through authentication?
• NAT with DHCP
• Frame Relay
• HDLC with encryption
• HDLC with CHAP
• PPP with PAP
* PPP with CHAP
27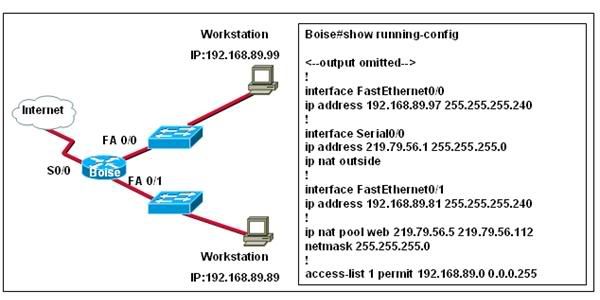
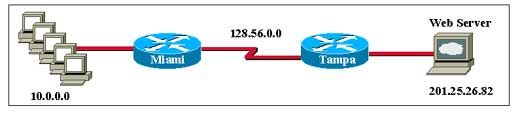
Refer to the exhibit. Which statements describe why the workstation with the IP address 192.168.89.99 cannot access the Internet? (Choose two.)
• The NAT outside interface is not configured properly.
* The NAT inside interface is not configured properly.
• The access control list does not include the IP address 192.168.1.99/28 to access the Internet.
• The NAT pool is not properly configured to use routable outside addresses.
* The NAT pool is not properly configured to use the access control list for NAT.
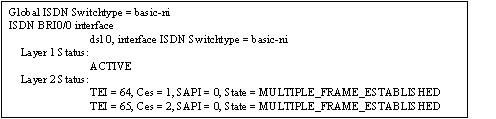
28 After the ISDN BRI interface is configured, which command can be used to verify that the router is communicating correctly with the ISDN switch?
• show dialer
* show isdn status
• show interfaces bri0/0:1
• show interfaces serial0/0.1
29 How are the settings for ISDN switch type and SPIDs determined for a BRI interface configuration?
• assigned by the network administrator
• randomly, so long as they are not duplicated on the network
• by trial and error
• dynamically via Inverse ARP
• assigned by IANA
* assigned by the service provider
30 A network administrator is having difficulty in establishing a serial link between a Cisco router and a router from another vendor. Both routers are configured for HDLC encapsulation. Which statements are true regarding this configuration? (Choose two.)
* The Cisco HDLC frame uses a proprietary "Type" field that may not be compatible with equipment of other vendors.
• HDLC requires a clock rate to be configured on the routers at both ends of the serial link.
* PPP encapsulation is recommended for serial links between equipment from multiple vendors.
• Usernames must be configured at both ends of the HDLC serial link.
• The HDLC vendor type must be enabled on the Cisco router.
• There is a mismatch in the HDLC authentication password configurations.
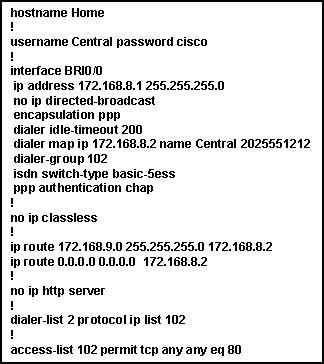
31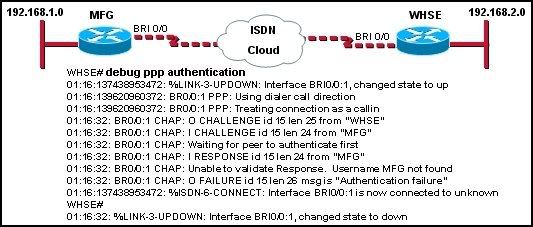
A system administrator is troubleshooting a connectivity issue between two routers in a new installation. The administrator enters the debug ppp authentication command on the WHSE router. The graphic shows a part of the output received. From this output, what is the most likely cause of this connectivity issue?
• There is not a route to the remote router.
• The ISDN circuit on the remote router has failed.
* The username/password was not properly configured on the WHSE router.
• The remote router has a different authentication protocol configured.
32 A system administrator needs to configure the regional office with ISDN for DDR connections to three remote sites. Each remote site requires different IP subnets, different encapsulations, and different authentication methods. The sites will not be connected at the same time. The company would like to accomplish this in the most cost effective manner. What method can the system administrator use to accomplish this task using the fewest B channels?
• Install and configure a PRI.
• Install and configure a BRI interface with separate SPIDs for each remote site.
• Install and configure a BRI with multiple switch types in global configuration.
* Install and configure a BRI using dialer profiles.
• Install and configure a separate BRI for each remote site.
33 Which IP addresses are defined by RFC 1918 as private addresses? (Choose three.)
• 172.55.16.0.16
* 172.17.0.0/16
• 224.200.175.0/24
* 192.168.168.0/22
• 10.88.179.0/29
• 17.250.0.0/16
34 Which of the following statements are correct regarding PAT? (Choose two.)
• PAT is the best method to provide consistent global addresses for network servers.
• PAT can only be configured to use one IP address, which is usually the IP address of the serial interface of the router.
• PAT uses unique source port numbers on the inside local IP address to distinguish between translations.
* PAT uses unique source port numbers on the inside global IP address to distinguish between translations.
* When PAT is configured to use a pool of IP addresses and exhausts the ports of the first IP address, the router will move to the next available IP address.
35 Which circuit-switched WAN technology is often used to provide a backup for a leased line and additional capacity during peak usage times?
• X.25
• DSL
* ISDN
• cable modem
36 Which of the following is the order for the three phases of establishing a PPP serial link with authentication?
• authentication, link-establishment, network layer protocols
• authentication, network layer protocols, link-establishment
• network layer protocols, link-establishment, authentication
• network layer protocols, authentication, link-establishment
* link-establishment, authentication, network layer protocols
• link-establishment, network layer protocols, authentication
37 What causes a DDR call to be placed?
• dial string
• DLCI
• idle time out
* interesting traffic
• PVC
38 A system administrator must provide Internet connectivity for 25 hosts at an insurance agency. The ISP has assigned two public IP addresses to this company. What can the administrator do to provide Internet access to all 25 users at the same time?
* Configure the router with dynamic NAT with PAT.
• Configure the router with dynamic NAT for 25 users.
• Configure the router with DHCP and static NAT.
• Configure the router with static NAT for all 25 users.
• This cannot be done with only two public addresses.
39
A network administrator must provide WAN connectivity between the Central office and three remote sites: East Branch, West Branch, and Remote. The East Branch and West Branch offices receive sales orders and transmit shipping confirmations to the Central office consistently throughout the day. The Remote office is staffed by one salesperson who travels through the northwestern territory. The salesperson occasionally needs to connect to the Central office for e-mail access. How should the network administrator connect these sites to the Central office? (Choose two.)
• Connect the East Branch and West Branch remote offices with ISDN connections.
* Connect the East Branch and West Branch offices with Frame Relay connections.
• Connect the East Branch and West Branch offices with POTS dial-up connections.
• Connect the Remote office with a Frame Relay connection.
• Connect the Remote office with an ISDN connection.
* Connect the Remote office with a POTS dial-up connection.
40 Which of the following ISDN protocols is responsible for call setup and call teardown?
• ITU-T Q.921
* ITU-T Q.931
• ITU-T I.430
• ITU-T I.431